
One of the latest trends in phishing consists of using fake sharefile sites to attempt to steal email credentials. These emails attempt to get the victim to click on a link to download an encrypted file. Once the link is clicked, the reader is directed to a fake login screen where they are prompted to indicate which email service they use.
Trends in Phishing
Recently, we’ve seen an uptick in attempted email phishing attacks. One of the latest trends in phishing consists of using fake sharefile sites to attempt to steal email credentials. These emails attempt to get the victim to click on a link to download an encrypted file. Once the link is clicked, the reader is directed to a fake login screen where they are prompted to indicate which email service they use. It is important to note that this page is designed to look legitimate.
Once the victim has chosen which email service they use, a sign in window opens up prompting the user to enter their email credentials. Again, this sign in window is completely customized to look like whichever email sign on page has been clicked. For example, the window that opens when Office 365 is chosen looks almost indistinguishable from the real thing to the untrained eye, and the same level of customization can be expected across other platforms as well. Even the logos used in phishing attacks often look exactly like the logos for the platform being mimicked. However, the logos used in phishing attacks may be dated, so it is important to remain aware of the most up-to-date logos in place on the platforms you use.
To the right are some examples of old Microsoft Office logos and how they have evolved over the years.
There are often some other noticeable differences that can be picked out as long as the user is paying close attention. For example, clicking on the Google sign in option opens a window that offers a choice between logging onto an organizational or individual account. This step is not part of the real Google sign-in process, and it is likely used to help the attackers distinguish personal accounts from business accounts.
The image below illustrates some other possible differences between a real Office 365 sign on page and a fake page created for phishing attacks. Note that the image of a phishing attempt on the left is using a dated logo, and the URL is not https so the web address is not marked “Secure” with the green padlock.
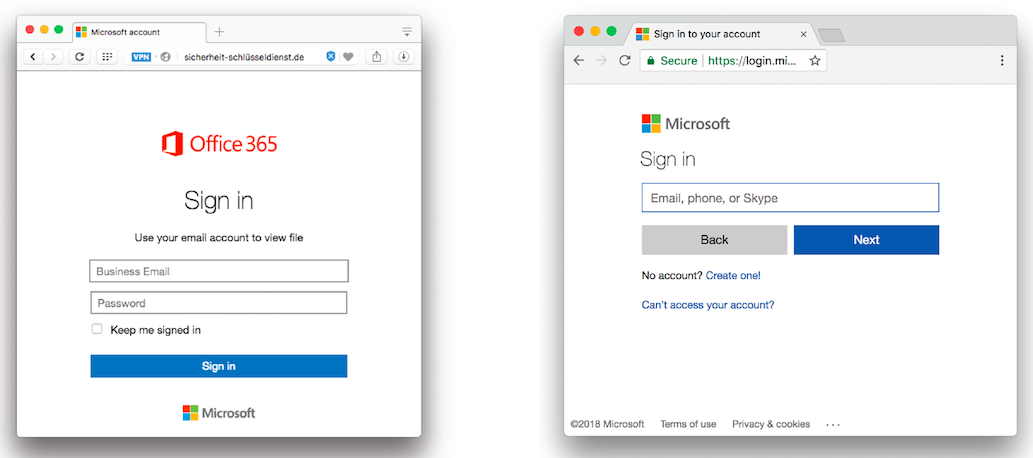
Research indicates that Office 365 users seem to be targeted most often, but this scheme also targets users of Google, Outlook, AOL, Yahoo!, and other email platforms.
Security Recommendations
Mandatory Multi-Factor Authentication for Office 365 accounts – Multi-factor authentication adds a second layer of security to user sign-ins and transactions by requiring more than one method of verification. Verification methods may consist of 2 or more of any of the following:
- A randomly generated pass code
- A phone call
- A smart card
- A biometric device
Awareness – Ensure that you and your co-workers are up-to-date on the latest trends in phishing. Since methods are changing constantly, it is important to be constantly aware of the risks involved. If you believe you may have given away your password through a phishing attack, it is vital that you change you password immediately.
Protect – Approximately 90% of all system breaches are preventable through basic security measures. Intellithought’s Phoenix Protects is a 3-tier security and recovery solution that guards against external and internal cyber threats.
Learn More about How to Recognize Phishing Attempts
Fill out the form below to get proactive about protecting your data.

